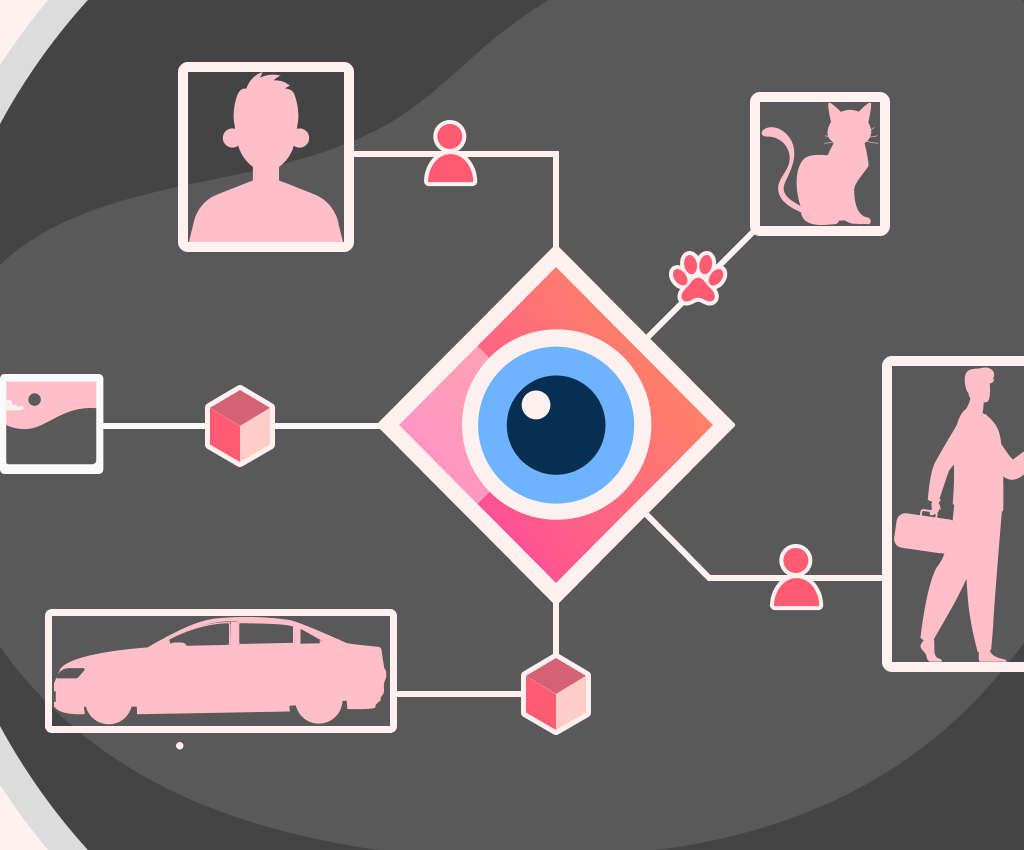
Computer Vision is a field of study that deals with enabling computers to interpret and understand visual information from the world in the same way that humans do, using digital images and videos. It involves techniques for acquiring, processing, a ...
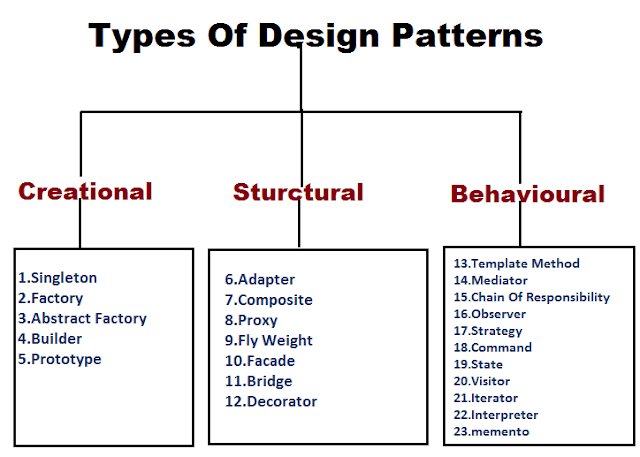
Software design patterns
Software design patterns offer reusable solutions to common software design problems. They provide elegant and flexible ways to solve recurring design problems, and you can apply them in various contexts. There are several categories of d ...
Software Development life cycle (SDLC)
SDLC the software development life cycle (SDLC) is a process that outlines the steps involved in developing software. The specific steps in the SDLC will vary depending on the specific method being used, but most methods include the following ...
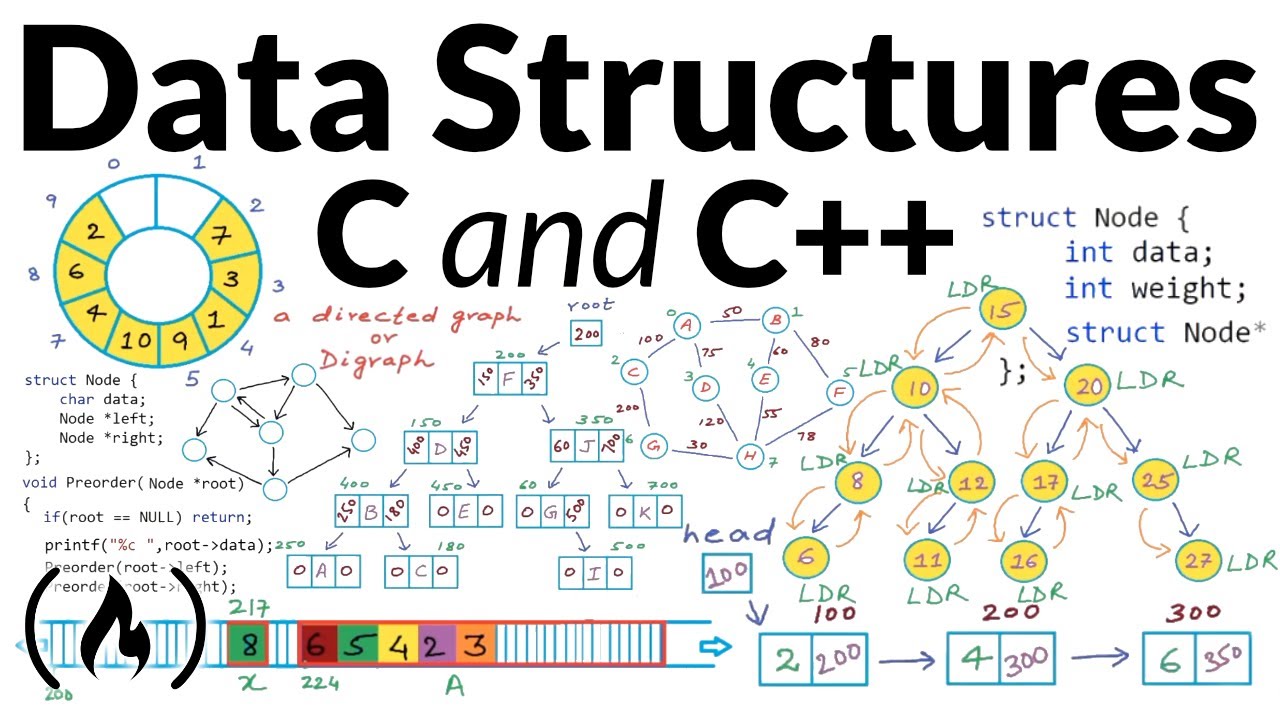
Data Structures
The data structure is a way of organizing and storing data in a computer so that it can be accessed and modified efficiently. Different types of data structures are suited to different kinds of applications, and some are highly specialized to sp ...
Flutter push notification using firebase (FCM)
FCM (Firebase Cloud Messaging) is a cross-platform messaging solution that lets you reliably deliver messages at no cost. It is provided by Google as part of the Firebase suite of tools. To use FCM in a Flutter app, you will need to use the fireb ...
JWT with Laravel
JSON Web Tokens (JWTs) are a popular way to authenticate users and transmit information about them between systems. In this post, we'll explore how to use JWTs with Laravel, a popular PHP framework for web application development. First, let' ...
What is JWT (JSON Web Token)
what is JWT (JSON Web Token) is a compact and self-contained way of transmitting information between parties as a JSON object. JWTs are often used to authenticate users and transmit information about them between systems, and are commonly used in si ...
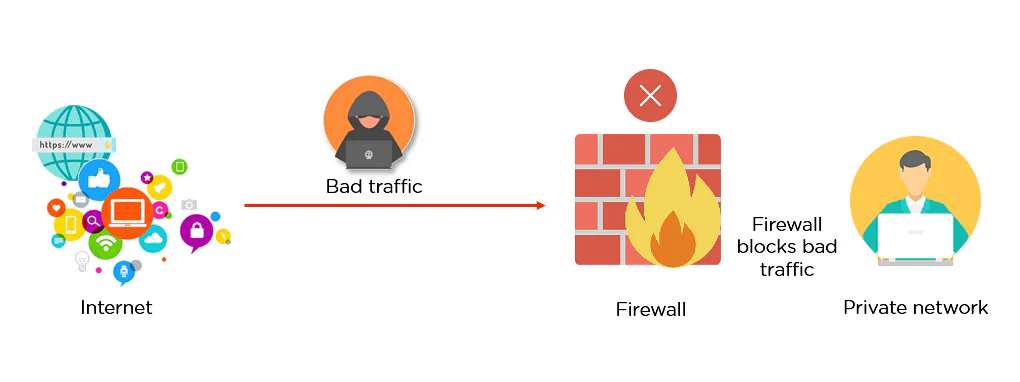
OWASP ZAP (Zed Attack Proxy)
What are Best Scanner tools? OWASP ZAP (Zed Attack Proxy) is an open-source web application security scanner that can be used to identify vulnerabilities in web applications. It can be used to perform both automated and manual security testing. ...
What is JSON
JSON (JavaScript Object Notation) is a lightweight data interchange format that is easy for humans to read and write and easy for machines to parse and generate. It is based on a subset of the JavaScript Programming Language, Standard ECMA-262 3rd E ...